Onboarding is not about compliance; it's about trust
Should security and convenience exclude each other in the customer onboarding process? Josje Fiolet, Digital Onboarding lead at INNOPAY, says “no”.
Security and convenience are often seen as diametrically opposed. However, with rapidly evolving technologies coming into play, this should no longer be the case. It’s time to realise that security and convenience are two sides of the same coin.
Establishing trust is the key to success
Organizations are struggling to find a healthy balance between security and convenience during the customer onboarding process. When we ask financial institutions what customer onboarding means to them, the answers differ from organization to organization. Some of them highlight the user experience, but most still focus on security and compliance. At INNOPAY we say"onboarding is not about compliance; it’s about trust". And here we are referring to mutual trust.
Onboarding is primarily seen as about the trust which the organization has in the prospect. Are we allowed to register the client? Can we adhere to our Know Your Customer (KYC) obligations and operate within the regulatory and risk framework?
But trust is a two-way street, and sometimes organizations forget that it’s also about the trust that the prospect has in them as an organization. Are they who they claim to be? The onboarding process should be rock solid, and it should be in line with the impression that the organization wants to convey. If an organisation claims to be an innovative and agile player, but the onboarding process contains multiple manual processes and takes weeks to complete, this is likely to result in distrust on the part of the prospect.
Challenger banks are leading; others must catch up quickly
Based on the results of INNOPAY's recent benchmark study, it becomes visible that newer and smaller banks, such as N26 and Monese, are outperforming the more established banks in the way they onboard new customers. The Benchmark focuses on the customer’s perspective and is based on two variables
-
The Effort it takes for the prospect to complete the onboarding process;
-
The Response of the organization to the prospect during the onboarding process.
An organization’s performance on these axes is determined by a number of questions, some of which are shown in Figure 1.
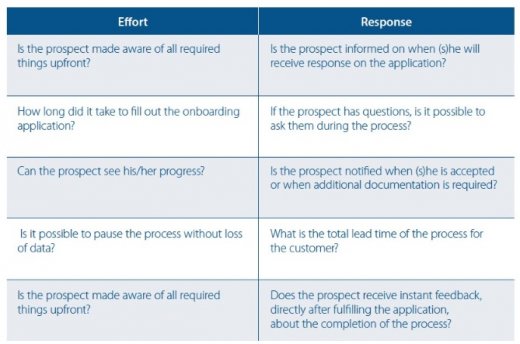
The results are not surprising because incumbent banks maintain a different risk profile compared to the challenger banks due to their higher volume of customers and their impact on the financial market. As such they are generally more hesitant to use online identification techniques.
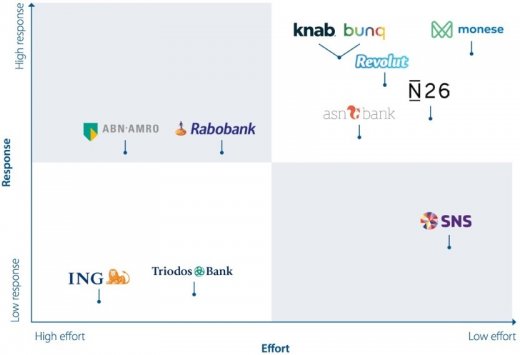
In practice there is often still a "better safe than sorry" approach at many organizations which continue to put more emphasis on adhering to KYC obligations. However, if they don’t transform their processes and embrace digital opportunities, they will soon seem old-fashioned to new customers. This doesn’t have to be the case. With evolving technologies, digital customer onboarding processes can be secure while also providing a user-friendly experience. Let's consider some ways to achieve this.
Organizations can consider a diverse range of technologies to enhance the process
When identifying a customer online, organizations focus on two questions:
-
Is the customer's document valid?
-
Is the person really who he/she claims to be?
To check the document's validity, there are already technologies in the market such as video identification and taking a picture of the ID document, but both require real people to analyse the document. A promising new solution is reading the chip of the document via NFC (Near-Field Communication). This solution is currently only available for Android operating systems, but it proves the document exists and the data quality is better than with the other techniques. When there is only a need for certain attributes, eID solutions can also be used. AMLD5 (Anti-Money Laundering Directive 5) currently makes explicit reference to the use of relevant trust services as set out in eIDAS.
To check if the person going through the process is indeed the same person as stated on the identification document, some form of facial recognition is required. However, facial recognition techniques are vulnerable to so-called spoofing attacks in which fake biometric samples are used. For facial recognition to be a secure system, liveness detection that guards against spoofing attacks is required. Liveness detection determines if the biometric being captured is an actual measurement from the authorised, live person who is present at the time of capture. Our facial recognition article elaborates upon different techniques for liveness, as shown below.
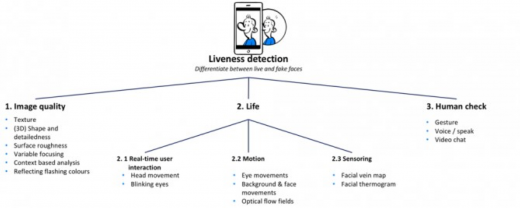
In practice, real-time user interactions and human checks are still the most common methods of identification. Image quality techniques are maturing, with a large Dutch bank being one of the first to use the flashing colour technique that detects if a photo or screen image is being presented instead of a real face.
To build a reliable profile of the customer, other techniques can also be considered. The trail of data that we leave behind may not be an identification method in itself but it can serve as additional step when building a reliable profile. For example, our activity on social networks can be used to provide a certain level of assurance of someone’s identity, and the account's profile picture can be matched with the picture in the identification document. Customers who are willing to share this type of data can be presented with a more seamless process. By providing these types of options to customers, it’s possible to give them greater control over the process.
And we should keep in mind that identity assurance during the lifetime of the client relationship is just as important as during the onboarding process. Is the behaviour of the customer congruent with the profile established during onboarding? Does their behaviour remain consistent from session to session? With continuous authentication techniques such as behavioural biometrics and behavioural profiling, we can reduce the burden on the onboarding process. There is a fair balance between mitigating the likelihood that something will occur, and the impact when it does. And that positively influences the customer experience.
Finding the best combination of technologies
Establishing mutual trust during and after the onboarding process relies on a sensible combination of multiple technologies and mitigating measures. These technologies and measures need to fit the risk profile of the organization, the type of service and the prospect. Start by bringing all relevant parties into the discussion. Engage with your business owners. Test and embrace new technologies. Explain to colleagues from legal and compliance what the technique is and what the potential risks and benefits are. Security professionals have an important role in bridging the gap between convenience and security. From the start, all these disciplines should be represented. Only with multidisciplinary teams can new, successful onboarding processes be defined. Processes in which convenience and security are considered to be two sides of the same coin.
If you are considering how to improve your customer onboarding process, feel free to contact us. We are more than happy to think with you and determine how we can help.




