It's about the personal data, stupid
Afraid of huge fines, organizations are pressuring themselves to prepare for GDPR (the General Data Protection Regulation) that will take effect on 25 May 2018. Probably, they have already conducted an initial privacy impact assessment (PIA), they will have assigned a local privacy officer, and they are planning or providing privacy awareness training sessions. Organizations are also developing privacy policies and procedures, and they are implementing the processes necessary to support all of this. However, it is securing the personal data what it’s really about.
How about the personal data itself?
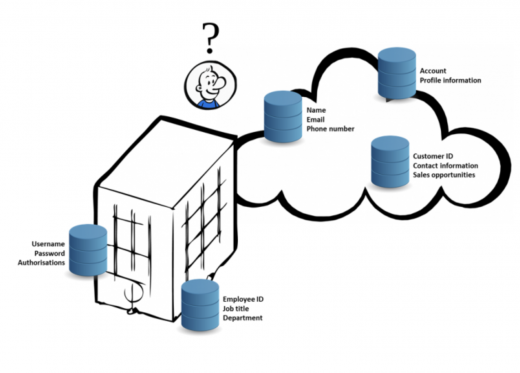
Organizations should not forget that GDPR and all other privacy regulations are meant to protect the privacy of individual persons. So in the end, it is the personal data of individuals (also known as personally identifiable information or PII, which is data that can be used to identify, contact, describe or locate an individual) that must be protected. To that end, GDPR requires controllers and processors to implement 'technical and organizational measures' to protect the personal data that they process. That is easier said than done, as data is stored somewhere, most probably scattered all over the organization and somewhere in the cloud, in storage volumes, databases, filesystems, email, and so on. Before any security controls can be implemented to protect the personal data, it needs to be identified and located. In cloud environments, there is the added complication of processing personal data owned by a specific organization, whilst leaving untouched the personal data belonging to other customers that might be located in the same storage volumes. To make it even more complicated, cloud providers sometimes do not even know themselves where the data of their customers is exactly stored.
How to locate personal data
Identifying and locating records of personal data can therefore be quite challenging. To determine and accurately inventory the personal data under their control, organizations can use a variety of methods. If the personal data is labelled with sufficient and accurate labels, then this will be of great help in the data discovery effort. Labelling is an absolute necessity when creating or collecting personal data. Label information should at least include the following:
- Source
- Confidentiality level
- Dissemination instructions
- Directions for handling
Another way of discovering personal data is based on metadata, also referred to as data about data. Examples of metadata include author, size, title, and date and time of creation and last modified. If the personal data is not properly labelled or should the metadata not provide enough grip, the data can be discovered based on the content itself. Discovery tools can be used to perform basic searches on terms such as ‘name’ or ‘contact’ or to perform more advanced pattern-matching searches.
Ownership
It goes without saying that all data, including personal data, that is used by the organization should have an owner who is responsible for categorizing, classifying and labelling the personal data. The owner is usually a business unit manager or department head who has created or collected the personal data, and who best understands for what purpose the data may and will be used by the organization. But the owner is also responsible for protecting the personal data. In other words, the data owner is also the owner of any risks that are applicable to the personal data, such as the risk of unauthorized access, in the context of privacy regulations also referred to as data leakage. This is always true, even when the personal data is stored somewhere in the cloud. The data owner, and ultimately the organization, is always legally liable for any compromise of personal data, even if the cloud provider has demonstrated negligence or ill will.
Protecting the personal data
The single most effective control here is encryption. Without encryption, it is impossible to protect personal data in a secure way, no matter what other security controls are put into place. It is encryption that is used to adequately protect the data both at rest and in transit, within the organization as well as in the cloud environment. Any data leakage of properly encrypted personal data is harmless. Encryption can also – and should – be used to securely dispose of personal data that is not needed anymore, especially in cloud environments. Encryption requires knowledge and expertise that organizations should heavily invest in. It involves a lot of aspects such as procedures to manage encryption keys and digital certificates, standards selection, definition of use cases, training and awareness, and last but not least technology.
Putting the customer in control
Identity & access management (IAM), in particular customer IAM (CIAM) is needed to facilitate access to personal data. IAM is used to grant authorised people the right access to information, based on principles as need-to-know and least privilege. Under GDPR, individuals must be informed about the processing of their personal data and, where applicable, must be able to give or withdraw their consent for this. With CIAM, it will be possible to implement consent management in a granular way, thus putting the customer in control. Like encryption, CIAM includes a great number of aspects such as authentication mechanisms, monitoring and reporting, deployment models (on-premise, identity as a service or hybrid), and user experience.
Is your organization really compliant with GDPR's security and control requirements? Feel free to contact us to find out.




